Malware is a form of application that performs nefarious activities. There are different types of DoS and DDoS attacks.

The 6 Types Of Cyber Attacks To Protect Against In 2018 Llrx Cyber Attack Cyber Security Threats Cyber Security
A type of malware they are unique pieces of code that can wreak havoc and spread from computer to computer.
. As more organizations allow their workers to access information from cell phones systems become weak against information theft or complete destruction of the network. A security consultant reported that using quid pro quo as part of a security test enabled him to obtain the usernames and passwords of 85 percent of employees in a target organization. Extra Precautions for Personnel.
There are two types of attacks passive attacks and active attacks. Keep in mind that the security of a network is as strong as its weakest link. Common phishing attacks lead to loss of extremely personal information such as social security numbers and credit card information.
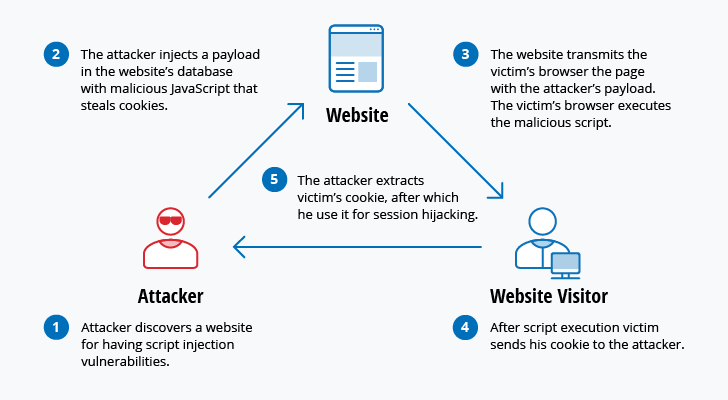
Phishing attack accounts for over 80 of reported cyber incidents. 4 Man in the Middle Attack. It is the attack in which some data will be injected into a web application to manipulate the.
Threat can be anything that can take advantage of a vulnerability to breach security and negatively alter erase harm object or objects of interest. In this article we have explored these ten different types of cyberattacks in detail. There are different types of password attacks like brute force attacks dictionary attacks and keylogger attacks.
In addition to identifying such attempts anti-spoofing software will stop them in their tracks. Information security attacks are unauthorized activities against the IT resources of government corporate or private so as to steal sensitive data destroy them or modify them. If an employee continues the hacker will have access to that information and will then use it to steal your assets.
In a passive attack. It is a form of attack wherein a hacker cracks your password with various programs and password cracking tools like Aircrack Cain Abel John the Ripper Hashcat etc. However some examples include the Brute-Force attack Dictionary attack Rainbow Table attack Credential Stuffing Password Spraying and the Keylogger attack.
An insecure application could expose users and systems to various types of damage. More than 71 of targeted attacks involve the use of spear phishing. In this attack an attacker exploits the use of the buffer space during a Transmission Control Protocol TCP session initialization handshake.
There are two types of attacks that are related to security namely passive and active attacks. DNS Spoofing is a type of computer security hacking. In Phishing an attacker tricks an unsuspecting target into handing over valuable information such.
Social engineering is a type of password attack that Data Insider defines as a strategy cyber attackers use that relies heavily on human interaction and often involves tricking people into breaking standard security practices Other types of password attacks include accessing a password database or outright guessing. 10 Types of Cyber Attacks That Cybercriminals Use 1. Passive attacks are not as harmful as they do not cause any altering or modification of data.
Malwares can be used for extortion. Methods of Cyber Attacks 1. Security awareness is the first line of defense against any social engineering technique.
TCP SYN flood attack. Top 20 Most Common Types of Cyber Attacks 1. Here we discuss the top 10 networking threats and attacks.
Spear phishing is a more sophisticated form of a phishing attack in which cybercriminals target only privileged users such as system administrators and C-suite executives. Man-in-the-middle MITM types of cyber attacks refer to breaches in cybersecurity that make it. And of course attackers will often try to use Phishing techniques to obtain a users password.
A denial-of-service DoS attack is designed to overwhelm the resources of a system to the. Evolution of Cyber Security. The most common are TCP SYN flood attack teardrop attack smurf attack ping-of-death attack and botnets.
DoS and DDoS Attacks. Computer viruses are one of the most common network security attacks that can cause sizeable damage to your data. Snooping on data eavesdropping is simple examples of passive attacks.
Information Security threats can be many like Software attacks theft of intellectual property identity theft theft of equipment or information sabotage and information extortion. Whereby a data is introduced into a DNS resolvers. Thankfully there are different solutions that detect the common types of spoofing attacks including ARP and IP spoofing.
Types of Cyber Attacks. When a malicious party uses vulnerabilities or lack of security features to their advantage to cause damage it is called an attackWell take a look at different types of attacks in this guide so you know what to look for when securing your application. These are the major types of cyber attacks you need to know about.
Cyber Security Attack Types Active and Passive Attacks. In an active attack an attacker tries to modify the content of the messages.
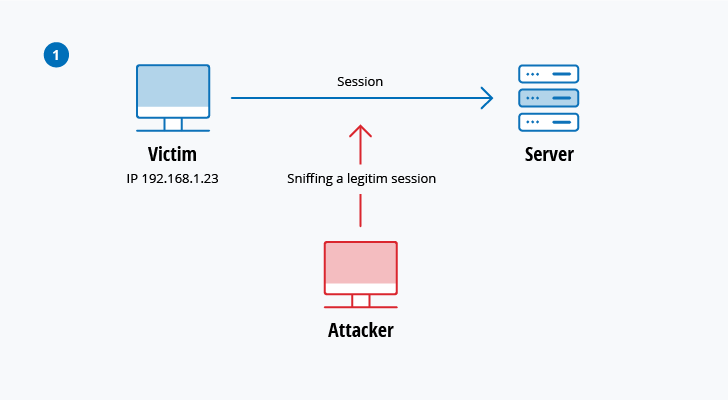
Top 10 Most Common Types Of Cyber Attacks
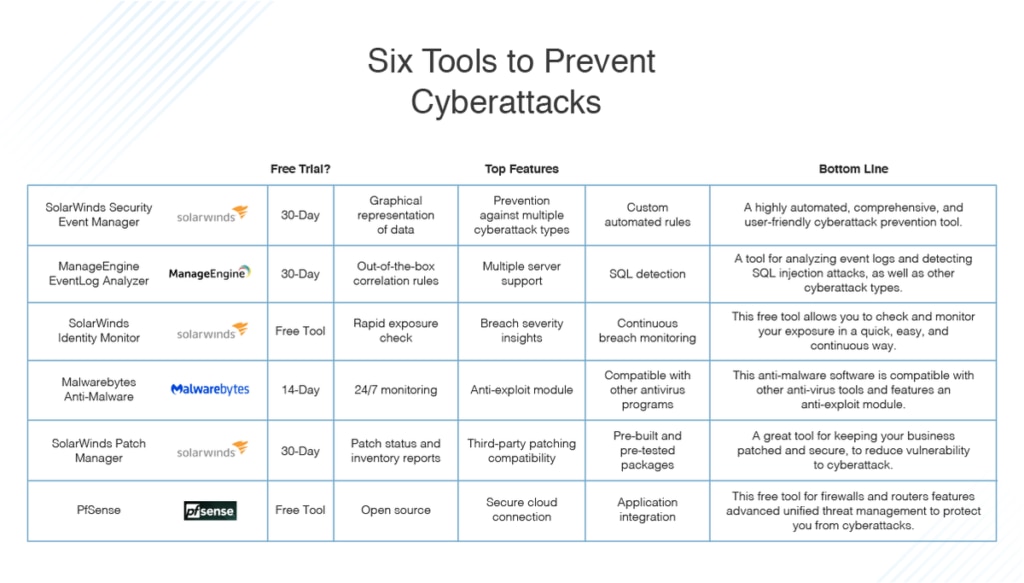
0 Comments